Kraken's Ingenious Sting: How They Caught North Korean State-Sponsored Hackers

Welcome to your ultimate source for breaking news, trending updates, and in-depth stories from around the world. Whether it's politics, technology, entertainment, sports, or lifestyle, we bring you real-time updates that keep you informed and ahead of the curve.
Our team works tirelessly to ensure you never miss a moment. From the latest developments in global events to the most talked-about topics on social media, our news platform is designed to deliver accurate and timely information, all in one place.
Stay in the know and join thousands of readers who trust us for reliable, up-to-date content. Explore our expertly curated articles and dive deeper into the stories that matter to you. Visit NewsOneSMADCSTDO now and be part of the conversation. Don't miss out on the headlines that shape our world!
Table of Contents
Kraken's Ingenious Sting: How They Caught North Korean State-Sponsored Hackers
The cryptocurrency world is notorious for its shadowy corners, but a recent operation shines a light on a particularly dark corner: North Korean state-sponsored hacking. Kraken, a prominent cryptocurrency exchange, has revealed a sophisticated sting operation that led to the identification and disruption of a hacking group linked to the Lazarus Group, a notorious North Korean entity known for its cyberattacks targeting financial institutions globally. This operation underscores the growing threat posed by state-sponsored cybercrime and the innovative methods employed to combat it.
A Multi-Year Investigation: Patience and Precision
The operation, spanning several years, involved painstaking investigation and meticulous planning. Kraken's security team, working in close cooperation with law enforcement agencies, identified suspicious activities consistent with Lazarus Group tactics. Instead of immediately confronting the hackers, Kraken employed a strategy of controlled engagement, allowing the hackers to believe they had successfully infiltrated the system. This "honeytrap" approach allowed Kraken to gather crucial evidence, tracing the hackers' digital footprints and uncovering their intricate network.
The Honeytrap: Luring the Lazarus Group
The heart of the operation involved creating a seemingly vulnerable system designed to attract the hackers. This "honeypot" mimicked a real Kraken system, tempting the Lazarus Group to attempt a data breach. The key here was realism; the honeypot needed to appear authentic enough to attract the hackers but secure enough to prevent any actual damage to Kraken's infrastructure. This required a high level of expertise in cybersecurity and a deep understanding of the Lazarus Group's modus operandi.
Tracking the Digital Trail: Unveiling the Network
Once the hackers engaged with the honeypot, Kraken’s security team meticulously tracked their every move. This involved sophisticated monitoring techniques to follow the digital bread crumbs, gathering crucial information about the hackers’ infrastructure, communication channels, and ultimately, their identity. This painstaking process allowed Kraken to build a compelling case, providing concrete evidence to law enforcement.
The Aftermath: A Blow to North Korean Cybercrime
The results of this operation represent a significant blow to North Korean state-sponsored hacking activities. By identifying and disrupting this specific group, Kraken has not only protected its own assets but has also contributed significantly to the global fight against cybercrime. This success demonstrates the critical role that private sector companies can play in countering these threats.
Lessons Learned and Future Implications:
- Collaboration is Key: The success of this operation highlights the importance of collaboration between private sector organizations and law enforcement agencies in combating cybercrime.
- Proactive Security Measures: This operation underscores the need for robust and proactive security measures within the cryptocurrency industry.
- The Evolving Threat Landscape: State-sponsored hacking is constantly evolving, requiring a constant adaptation of defensive strategies.
Kraken’s ingenious sting operation serves as a powerful case study in how to effectively counter sophisticated state-sponsored cyberattacks. It emphasizes the importance of proactive security measures, international cooperation, and innovative approaches to combating the ever-evolving threat landscape of digital crime. The details of the operation, while shrouded in some secrecy to protect ongoing investigations, offer a glimpse into the ongoing battle against North Korean cybercrime and the crucial role private entities play in this fight. The future of cybersecurity relies on such innovative strategies and strong collaborative efforts.

Thank you for visiting our website, your trusted source for the latest updates and in-depth coverage on Kraken's Ingenious Sting: How They Caught North Korean State-Sponsored Hackers. We're committed to keeping you informed with timely and accurate information to meet your curiosity and needs.
If you have any questions, suggestions, or feedback, we'd love to hear from you. Your insights are valuable to us and help us improve to serve you better. Feel free to reach out through our contact page.
Don't forget to bookmark our website and check back regularly for the latest headlines and trending topics. See you next time, and thank you for being part of our growing community!
Featured Posts
-
 Tesla Robotaxi Approved Statewide In Texas What This Means For Drivers And Passengers
May 05, 2025
Tesla Robotaxi Approved Statewide In Texas What This Means For Drivers And Passengers
May 05, 2025 -
 Single Infrared Beam Enables Transmission Of Nearly 2 Million Concurrent Netflix Hd Streams
May 05, 2025
Single Infrared Beam Enables Transmission Of Nearly 2 Million Concurrent Netflix Hd Streams
May 05, 2025 -
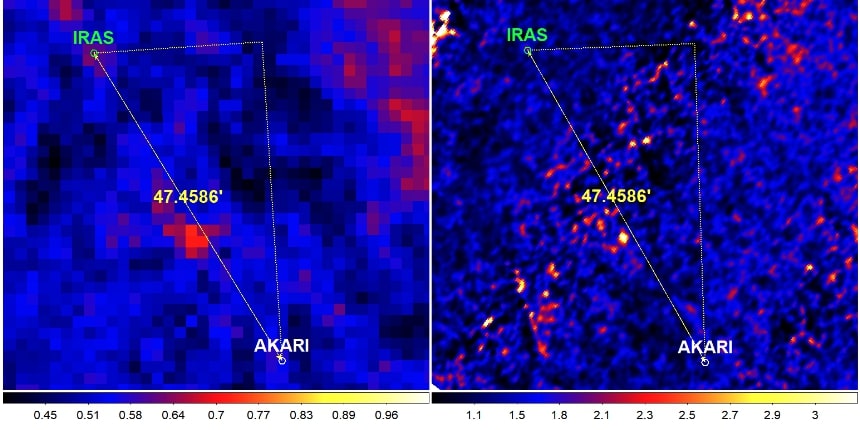 Could Planet Nine Exist Analysis Of Iras And Akari Infrared Observations
May 05, 2025
Could Planet Nine Exist Analysis Of Iras And Akari Infrared Observations
May 05, 2025 -
 Injury Scare For Jets Ehlers Drops Jersey Raises Concerns Ahead Of Crucial Game 6
May 05, 2025
Injury Scare For Jets Ehlers Drops Jersey Raises Concerns Ahead Of Crucial Game 6
May 05, 2025 -
 The Last Of Us Season 2 Episode 4 Plot Predictions Cast And Where To Watch
May 05, 2025
The Last Of Us Season 2 Episode 4 Plot Predictions Cast And Where To Watch
May 05, 2025
