Web3 Security: Why AI Models With Key Access Are A High-Risk Strategy

Welcome to your ultimate source for breaking news, trending updates, and in-depth stories from around the world. Whether it's politics, technology, entertainment, sports, or lifestyle, we bring you real-time updates that keep you informed and ahead of the curve.
Our team works tirelessly to ensure you never miss a moment. From the latest developments in global events to the most talked-about topics on social media, our news platform is designed to deliver accurate and timely information, all in one place.
Stay in the know and join thousands of readers who trust us for reliable, up-to-date content. Explore our expertly curated articles and dive deeper into the stories that matter to you. Visit NewsOneSMADCSTDO now and be part of the conversation. Don't miss out on the headlines that shape our world!
Table of Contents
Web3 Security: Why AI Models with Key Access Are a High-Risk Strategy
The decentralized promise of Web3 is tantalizing: a future of secure, transparent, and user-controlled data. But the rapid adoption of artificial intelligence (AI) within this nascent ecosystem presents a significant security challenge. Granting AI models direct access to private keys, a strategy touted by some as a path to automation and efficiency, is a high-risk approach fraught with potential vulnerabilities. This article explores why this strategy is fundamentally flawed and what safer alternatives Web3 developers should consider.
The Allure of AI-Powered Automation in Web3
The appeal of using AI to manage aspects of Web3 applications is undeniable. AI could potentially automate tasks like:
- Transaction signing: Automating the process of signing transactions, speeding up interactions and reducing user friction.
- Portfolio management: Optimizing investment strategies based on market trends and user preferences.
- Smart contract auditing: Identifying potential vulnerabilities in smart contracts before deployment.
However, the convenience offered by these automated systems comes at a steep price if implemented using the wrong approach. The primary concern revolves around the security risks associated with granting AI models access to private keys.
The Critical Vulnerability: Private Key Exposure
Private keys are the bedrock of Web3 security. They control access to digital assets like cryptocurrency and NFTs. Compromising a private key is equivalent to losing complete control over associated assets. Giving an AI model direct access to these keys presents a catastrophic vulnerability.
Here's why:
- AI model vulnerabilities: AI models themselves are susceptible to attacks. Malicious actors could exploit vulnerabilities in the model's code or training data to gain unauthorized access to private keys.
- Data breaches: A data breach affecting the system storing or managing the AI model could expose private keys, leading to widespread theft.
- Lack of transparency: The internal workings of complex AI models can be opaque, making it difficult to audit their security and identify potential weaknesses.
- Third-party dependencies: AI models often rely on third-party libraries and services, introducing additional points of potential failure and attack.
Safer Alternatives for Integrating AI in Web3
Instead of granting direct key access, Web3 developers should explore alternative strategies that prioritize security:
- Multi-signature wallets: These wallets require multiple signatures to authorize transactions, mitigating the risk of a single compromised key.
- Hardware security modules (HSMs): HSMs provide a secure environment for storing and managing private keys, isolating them from the AI model.
- Secure enclaves: These isolated processing environments within CPUs can protect sensitive operations, like signing transactions, from external access.
- Decentralized Identity (DID) systems: Utilizing DID for authentication and authorization minimizes the reliance on private keys for many operations.
The Future of AI and Web3 Security
The integration of AI in Web3 holds immense potential, but only if approached with a strong emphasis on security. Prioritizing security best practices, employing robust authentication methods, and using alternative strategies for managing private keys are critical for safeguarding the integrity and trust of the Web3 ecosystem. The allure of automation should never outweigh the fundamental need to protect user assets and maintain the decentralized ethos of Web3. Ignoring these risks could lead to devastating consequences and erode user confidence in the entire Web3 space. The future of this innovative technology depends on its ability to balance innovation with unwavering security.

Thank you for visiting our website, your trusted source for the latest updates and in-depth coverage on Web3 Security: Why AI Models With Key Access Are A High-Risk Strategy. We're committed to keeping you informed with timely and accurate information to meet your curiosity and needs.
If you have any questions, suggestions, or feedback, we'd love to hear from you. Your insights are valuable to us and help us improve to serve you better. Feel free to reach out through our contact page.
Don't forget to bookmark our website and check back regularly for the latest headlines and trending topics. See you next time, and thank you for being part of our growing community!
Featured Posts
-
 Data Sovereignty And The Eu Cloud Why Decentralization Matters
May 03, 2025
Data Sovereignty And The Eu Cloud Why Decentralization Matters
May 03, 2025 -
 Grok Ai By Elon Musk Microsofts Hosting Signals A Major Ai Partnership
May 03, 2025
Grok Ai By Elon Musk Microsofts Hosting Signals A Major Ai Partnership
May 03, 2025 -
 How To Watch Caitlin Clark Play Indiana Fever Vs Washington Mystics Game Time And Tv Info
May 03, 2025
How To Watch Caitlin Clark Play Indiana Fever Vs Washington Mystics Game Time And Tv Info
May 03, 2025 -
 Mlb Daily Picks Fernando Tatis Jr Sleeper Potential On May 2nd
May 03, 2025
Mlb Daily Picks Fernando Tatis Jr Sleeper Potential On May 2nd
May 03, 2025 -
 The Walking Dead Dead City How Boston Became The Shows Apocalyptic New York City
May 03, 2025
The Walking Dead Dead City How Boston Became The Shows Apocalyptic New York City
May 03, 2025
Latest Posts
-
 Ufc Espn 67 Quang Le Scores Impressive Submission Victory Over Gaston Bolanos
May 04, 2025
Ufc Espn 67 Quang Le Scores Impressive Submission Victory Over Gaston Bolanos
May 04, 2025 -
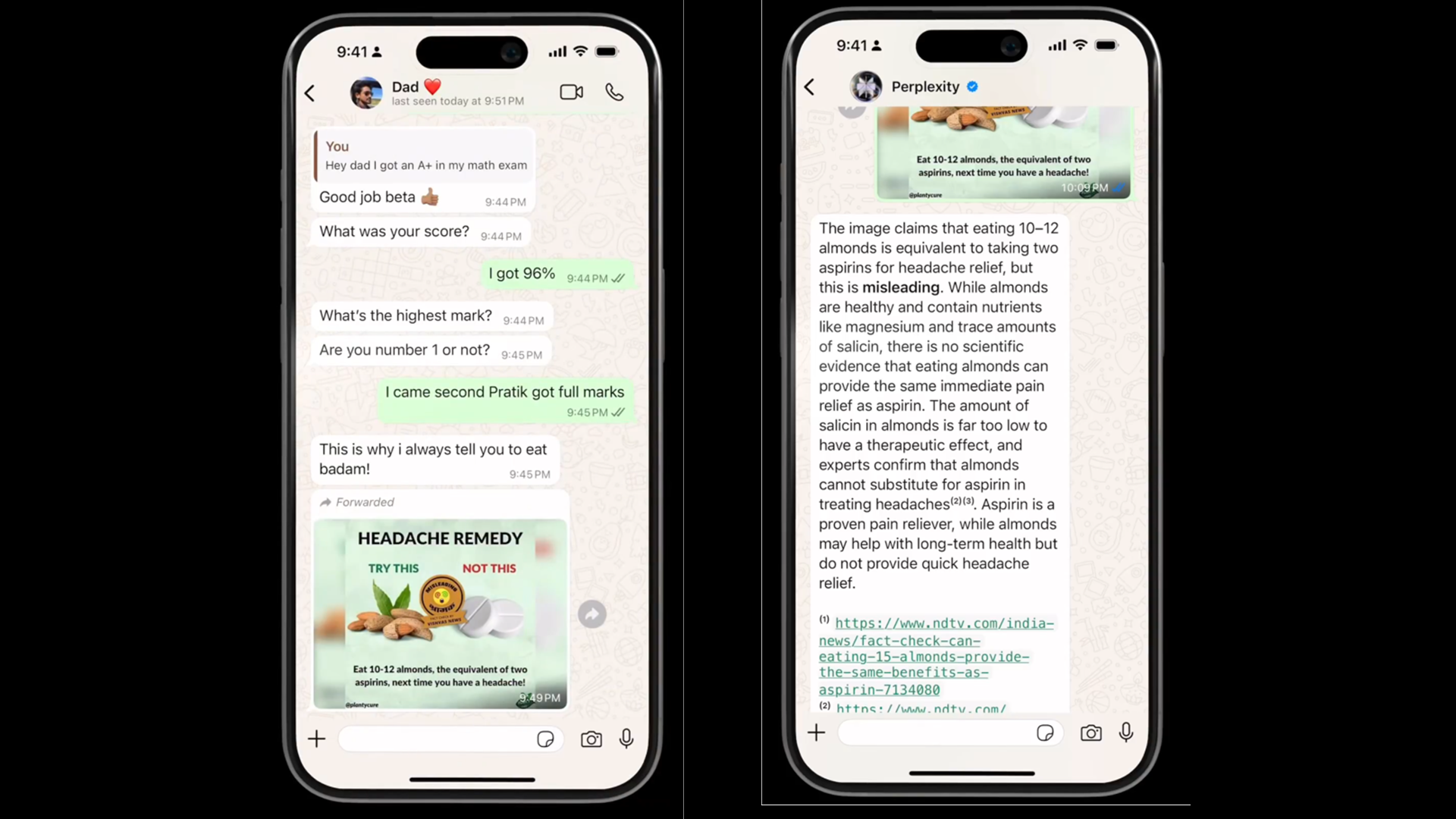 How To Fact Check Any Message On Whats App
May 04, 2025
How To Fact Check Any Message On Whats App
May 04, 2025 -
 Decoding Black Dandyism A Deep Dive Into The Met Galas Style Statement
May 04, 2025
Decoding Black Dandyism A Deep Dive Into The Met Galas Style Statement
May 04, 2025 -
 Avalanche Conquering Past Trauma To Achieve Success
May 04, 2025
Avalanche Conquering Past Trauma To Achieve Success
May 04, 2025 -
 Sui Blockchain Welcomes New Web3 Gaming Stablecoin
May 04, 2025
Sui Blockchain Welcomes New Web3 Gaming Stablecoin
May 04, 2025
