Effective Vulnerability Management: A Critical Security Response To INE's Alert

Welcome to your ultimate source for breaking news, trending updates, and in-depth stories from around the world. Whether it's politics, technology, entertainment, sports, or lifestyle, we bring you real-time updates that keep you informed and ahead of the curve.
Our team works tirelessly to ensure you never miss a moment. From the latest developments in global events to the most talked-about topics on social media, our news platform is designed to deliver accurate and timely information, all in one place.
Stay in the know and join thousands of readers who trust us for reliable, up-to-date content. Explore our expertly curated articles and dive deeper into the stories that matter to you. Visit NewsOneSMADCSTDO now and be part of the conversation. Don't miss out on the headlines that shape our world!
Table of Contents
Effective Vulnerability Management: A Critical Security Response to INE's Alert
INE's recent security alert highlights a critical need for robust vulnerability management strategies. Ignoring vulnerabilities leaves organizations exposed to devastating cyberattacks, data breaches, and significant financial losses. This article explores effective vulnerability management practices and how organizations can proactively mitigate risks in the wake of such alerts.
The recent alert from the INE (insert full name of INE here, e.g., Instituto Nacional de Estadística) underscored the urgent need for organizations to prioritize vulnerability management. The alert (cite the specific alert if possible, including a link) highlighted specific vulnerabilities impacting [mention the affected systems/software]. This serves as a stark reminder that even seemingly minor vulnerabilities can be exploited by sophisticated cybercriminals.
Understanding Vulnerability Management
Vulnerability management is a proactive process encompassing identifying, assessing, prioritizing, and remediating security weaknesses in IT systems and applications. It's more than just patching; it's a holistic approach that integrates various security measures to minimize risk. Effective vulnerability management involves:
-
Regular Vulnerability Scanning: Employ automated tools to identify potential vulnerabilities across your entire IT infrastructure. This includes network devices, servers, applications, and endpoints. Consider using a mix of internal and external scanning to gain a comprehensive view.
-
Vulnerability Assessment: Analyze identified vulnerabilities to determine their severity, exploitability, and potential impact on your organization. Prioritize critical vulnerabilities based on factors like the likelihood of exploitation and potential damage.
-
Patch Management: Implement a robust patch management process to promptly address identified vulnerabilities. This requires a coordinated effort across different teams and departments, ensuring that patches are applied quickly and efficiently while minimizing disruption to services.
-
Risk Mitigation: Develop and implement risk mitigation strategies for vulnerabilities that cannot be immediately patched. This might involve implementing security controls like firewalls, intrusion detection systems, or access control measures.
-
Continuous Monitoring: Continuously monitor your systems for new vulnerabilities and remediate them as they are discovered. The threat landscape is constantly evolving, and proactive monitoring is crucial to stay ahead of emerging threats.
Beyond Patching: A Multi-Layered Approach
Simply patching vulnerabilities isn't enough. A truly effective vulnerability management program necessitates a multi-layered approach that integrates various security best practices:
-
Security Awareness Training: Educate employees about common cyber threats and best practices to prevent social engineering attacks and phishing scams that could expose vulnerabilities.
-
Strong Access Control: Implement strict access control policies to limit access to sensitive systems and data, minimizing the impact of a successful breach.
-
Incident Response Plan: Develop and regularly test a comprehensive incident response plan to effectively handle security incidents and minimize their impact.
-
Regular Security Audits: Conduct regular security audits to assess the effectiveness of your vulnerability management program and identify areas for improvement.
The Cost of Inaction
Failing to implement effective vulnerability management exposes organizations to a range of significant risks, including:
- Data breaches: Leading to loss of sensitive customer data, financial penalties, and reputational damage.
- Financial losses: Including costs associated with remediation, legal fees, and business disruption.
- Compliance violations: Non-compliance with relevant regulations and standards can result in hefty fines.
- Reputational damage: A data breach or security incident can severely damage an organization's reputation and erode customer trust.
INE's alert serves as a wake-up call. Proactive and comprehensive vulnerability management is not a luxury; it's a necessity in today's threat landscape. By implementing the strategies outlined above, organizations can significantly reduce their exposure to cyber threats and protect their valuable assets. Don't wait for the next alert—start strengthening your security posture today.

Thank you for visiting our website, your trusted source for the latest updates and in-depth coverage on Effective Vulnerability Management: A Critical Security Response To INE's Alert. We're committed to keeping you informed with timely and accurate information to meet your curiosity and needs.
If you have any questions, suggestions, or feedback, we'd love to hear from you. Your insights are valuable to us and help us improve to serve you better. Feel free to reach out through our contact page.
Don't forget to bookmark our website and check back regularly for the latest headlines and trending topics. See you next time, and thank you for being part of our growing community!
Featured Posts
-
 Investing In 2025 A Head To Head Analysis Of Micro Strategy Mstr And Bitcoin Btc
May 18, 2025
Investing In 2025 A Head To Head Analysis Of Micro Strategy Mstr And Bitcoin Btc
May 18, 2025 -
 Sensationssieg Crystal Palace Triumphiert Im Fa Cup Gegen Manchester City
May 18, 2025
Sensationssieg Crystal Palace Triumphiert Im Fa Cup Gegen Manchester City
May 18, 2025 -
 Increased Security At Ottawa City Hall New Measures Begin May 26th
May 18, 2025
Increased Security At Ottawa City Hall New Measures Begin May 26th
May 18, 2025 -
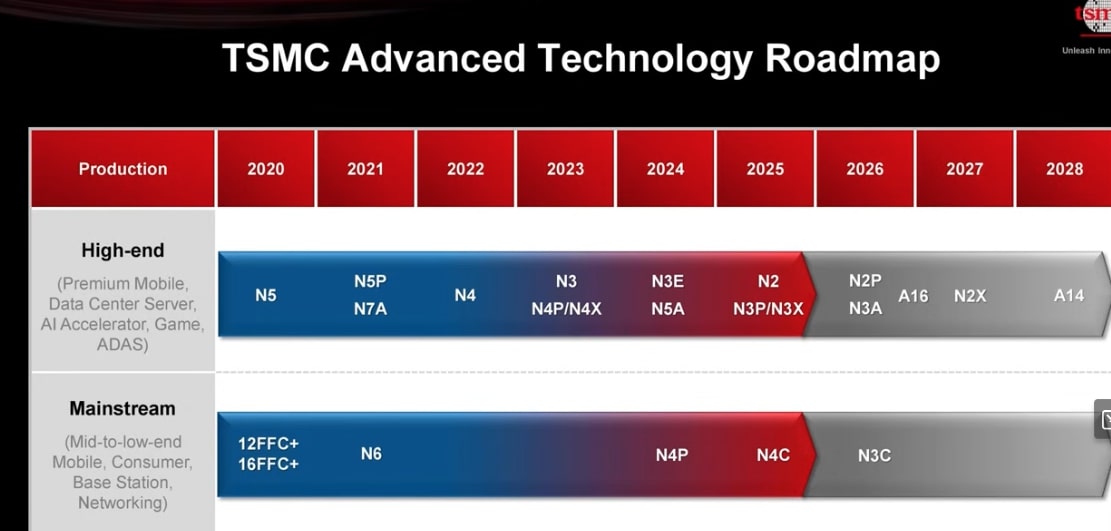 Tsmc 2025 Symposium 1 4nm Technology And The Semiconductor Roadmap To 2028
May 18, 2025
Tsmc 2025 Symposium 1 4nm Technology And The Semiconductor Roadmap To 2028
May 18, 2025 -
 Liga 3 Sporting B Promove Se Belenenses Despede Se Sem Play Off
May 18, 2025
Liga 3 Sporting B Promove Se Belenenses Despede Se Sem Play Off
May 18, 2025
Latest Posts
-
 Serie A Preview Genoa Vs Atalanta Predicted Xi And Match Outcome
May 18, 2025
Serie A Preview Genoa Vs Atalanta Predicted Xi And Match Outcome
May 18, 2025 -
 My Smart Home Runs On Lasers A Practical Assessment
May 18, 2025
My Smart Home Runs On Lasers A Practical Assessment
May 18, 2025 -
 Crystal Palace Manchester City Live Fa Cup Final Coverage
May 18, 2025
Crystal Palace Manchester City Live Fa Cup Final Coverage
May 18, 2025 -
 Where To Watch Ou Vs California Softball Game Today Ncaa Tournament Details
May 18, 2025
Where To Watch Ou Vs California Softball Game Today Ncaa Tournament Details
May 18, 2025 -
 Glasners Pokalambitionen Frankfurt Kaempft Um Den Pokal
May 18, 2025
Glasners Pokalambitionen Frankfurt Kaempft Um Den Pokal
May 18, 2025
